39 dmz network diagram example
Dmz Network Diagram Example - Diagram Sketch Computer Network Architecture Computer And Network Examples Computer Network Cisco Networking Network Architecture. Dmz Example Build A Dmz To Protect Networks With A Firewall Udr And Nsg Cloud Services Networking Clouds. Ip Dns Gateway Networking Computer Technology Computer Network Learn Computer Coding. MZ and DMZ Zone [classic] - Creately MZ and DMZ Zone [classic] Use Creately's easy online diagram editor to edit this diagram, collaborate with others and export results to multiple image formats. You can edit this template and create your own diagram. Creately diagrams can be exported and added to Word, PPT (powerpoint), Excel, Visio or any other document.
What is a DMZ (networking)? | Barracuda Networks In computer security, a DMZ Network (sometimes referred to as a "demilitarized zone") functions as a subnetwork containing an organization's exposed, outward-facing services. It acts as the exposed point to an untrusted networks, commonly the Internet. The goal of a DMZ is to add an extra layer of security to an organization's local area ...

Dmz network diagram example
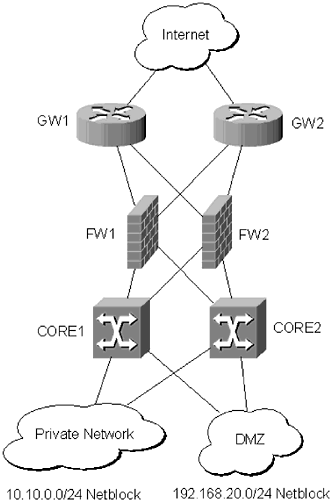
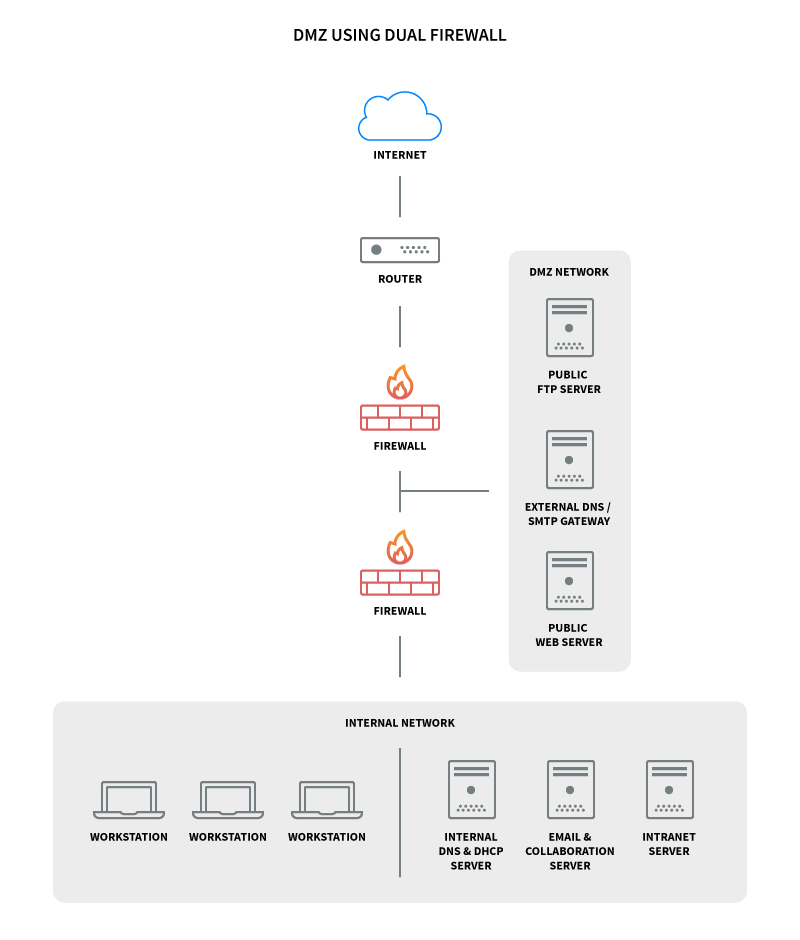
Firewall DMZ Configuration | EdrawMax Editable Templates The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network). It prevents outside users from gaining direct access to an organization's internal network while not ... Web application network diagram example for online ... The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network). docs.microsoft.com › en-us › azureImplement a secure hybrid network - Azure Architecture Center ... Network security groups.Use security groups to restrict network traffic within the virtual network. For example, in the deployment provided with this reference architecture, the web tier subnet allows TCP traffic from the on-premises network and from within the virtual network; the business tier allows traffic from the web tier, and the data tier allows traffic from the business tier.
Dmz network diagram example. Learning to Diagram a Secure Network | by Katrina K. | Medium Figuring out how to diagram a network f o r the first time was a bit overwhelming, but what helped was to understand the borders and components of the external (public), demilitarized zone ... How to Create a Basic DMZ (Demilitarized Zone) Network in ... This physical network example uses 3 ports: 1 for the WAN, 1 for the LAN, and 1 for the DMZ network. Assign DMZ Interface To assign a new interface for the DMZ network, go to the "Interfaces > Assignments" page. At the bottom of the page you will see the "New interface" section. Select the appropriate physical port from the dropdown box. PDF Secure Network Design: Designing a DMZ & VPN • A network added between a protected network and an external network in order to provide an additional layer of security • A DMZ is sometimes called a "Perimeter network" or a "Three-homed perimeter network. • A DMZ is an example of the Defense-in-Depth principle. -no one thing, no two things, will ever provide total security. Cisco ASA DMZ Configuration Example - IT Network ... Cisco ASA DMZ Configuration Example - IT Network Consulting | Design, Deploy and Support | San Diego.
Network architecture diagrams using UML - overview of ... The example of the network diagram below shows network architecture with configuration called "two firewall demilitarized zone". Demilitarized zone ( DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network). How does a DMZ network work? - AskingLot.com The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone ( DMZ ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network ). firewalls - Public DMZ network architecture - Information ... The two are functionally equivalent - the DMZ is effectively in a sandwich, as it has to have connections from the outside world firewalled, but also have firewalls restricting access from it to the internal network. While the latter diagram is often what happens (for cost reasons - you need less firewalls) the first one is considered safer as ... › labs › lab18-asa-dmzASA 5506-X DMZ configuration - Packet Tracer Network Oct 05, 2014 · Packet Tracer 7.2 DMZ lab using Cisco ASA 5506 firewall to securely connect internet users to public web server and secure the campus LAN network. AutoNAT configuration with network object for port address translation in Cisco ASA 5506 included in the lab.
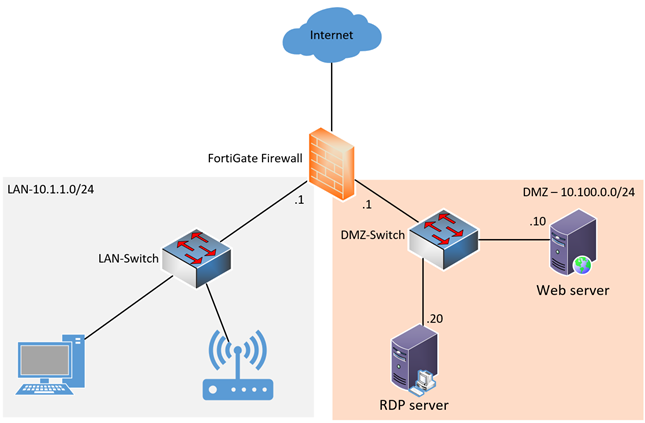
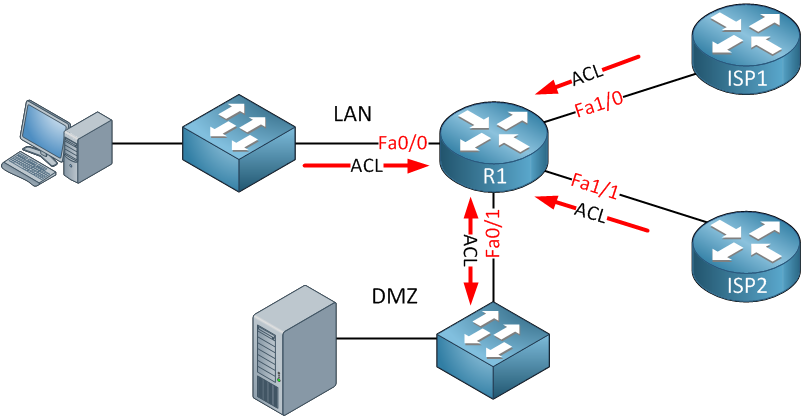
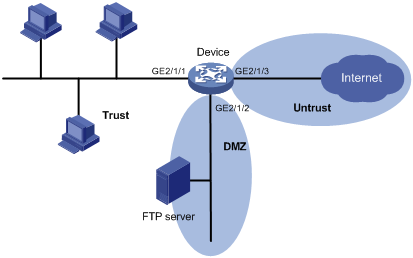
PDF Defense Information Systems Network (Disn) Connection ... Network (DRSN) now Multilevel Secure Voice. Deleted DISN Video Services (DVS). Added DOD IN and DISN clarification. Added discussion on NIPRNet Federated Gateway (NFG), SIPRNet Releasable De-Militarized Zone (REL DMZ), and SIPRNet Federal DMZ (FED DMZ). Removed previous language regarding the Connection Approval Office performing risk assessments. Network Design Scenario #2: DMZ Design The diagram highlights the simple traffic paths: outside can access the DMZ server but not the internal hosts, and if hosts need to access the DMZ they can. Moreover, the default interface level policy will not allow the untrusted network to source traffic towards the trusted network. DMZ Network: What Is a DMZ & How Does It Work? | Okta A demilitarized zone network, or DMZ, is a subnet that creates an extra layer of protection from external attack. Network administrators must balance access and security. Your employees must tap into data outside of the organization, and some visitors need to reach into data on your servers. But some items must remain protected at all times. What is DMZ switch? - TreeHozz.com Network Diagram Example. UML provides no special kind of diagram to describe logical or physical network architecture of the designed or existing system. Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network).
What's DMZ Network? Architecture of DMZ Networks ... DMZ ( (DeMilitarized Zone) is essentially a military and political term meaning a civilian area. The most famous example of a demilitarized zone right now is the demilitarized zone on the border between South Korea and North Korea: In network security, a DMZ is a physical or logical subnetwork that contains and exposes an organization's ...
Local area network (LAN). Computer and Network Examples ... A local area network (LAN) is a devices network that connect with each other in the scope of a home, school, laboratory, or office. Usually, a LAN comprise computers and peripheral devices linked to a local domain server. All network appliances can use a shared printers or disk storage. A local area network serve for many hundreds of users. Typically, LAN includes many wires and cables that ...
What is a DMZ in Networking? - SearchSecurity Examples of DMZs Some of the various ways DMZs are used include the following: Cloud services. Some cloud services, such as Microsoft Azure, use a hybrid security approach in which a DMZ is implemented between an organization's on-premises network and the virtual network.
plantuml.com › nwdiagNetwork diagram (nwdiag) - PlantUML.com nwdiag has been created by Takeshi Komiya and allows to quickly draw network diagrams. So we thank him for his creation! Since the syntax is clear and simple, this has been integrated within PlantUML. We reuse here the examples that Takeshi has documented.
Simple DMZ [classic] | Creately Simple DMZ [classic] Use Creately's easy online diagram editor to edit this diagram, collaborate with others and export results to multiple image formats. You can edit this template and create your own diagram. Creately diagrams can be exported and added to Word, PPT (powerpoint), Excel, Visio or any other document.
DMZs for dummies - ZDNet For example, you can allow HTTP to the Web-server on your DMZ, but not allow HTTP to your internal network. Systems in the DMZ should be as securely locked down as you can make them.
docs.microsoft.com › en-us › azureThe virtual datacenter: A network perspective - Cloud ... Mar 07, 2022 · The preceding diagram shows the enforcement of two perimeters with access to the internet and an on-premises network, both resident in the DMZ hub. In the DMZ hub, the perimeter network to internet can scale up to support many lines of business, using multiple farms of Web Application Firewalls (WAFs) or Azure Firewalls.
Configuring DMZ - Cisco Configuring DMZ. Use the Networking > DMZ page to configure a Demarcation Zone or Demilitarized Zone (DMZ). A DMZ is a sub-network that is behind the firewall but that is open to the public. By placing your public services on a DMZ, you can add an additional layer of security to the LAN.
Designing a DMZ for Azure Virtual Machines | Petri IT ... May 10, 2016 · A DMZ using Azure network security groups (Image Credit: Microsoft) The benefit of this design is that it is very simple. The drawback of this design is that it assumes that your potential hackers ...
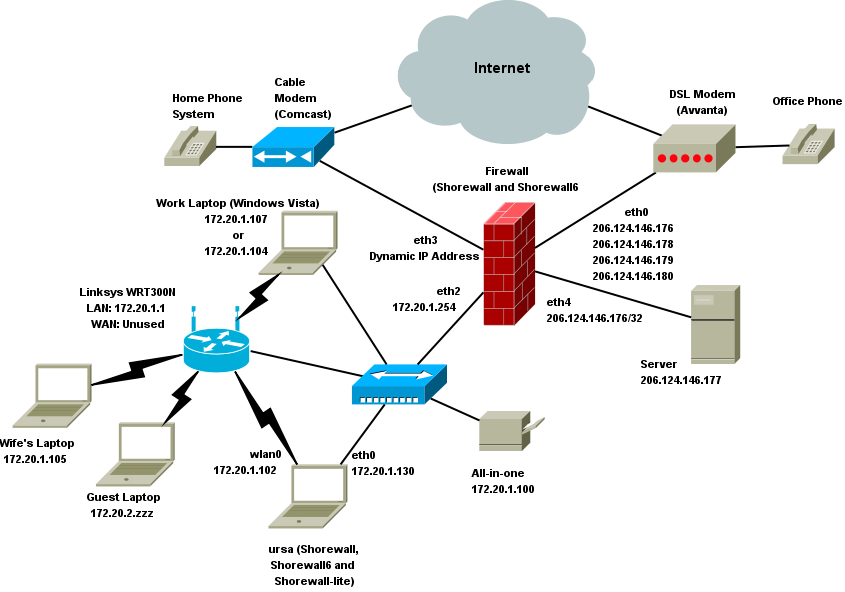
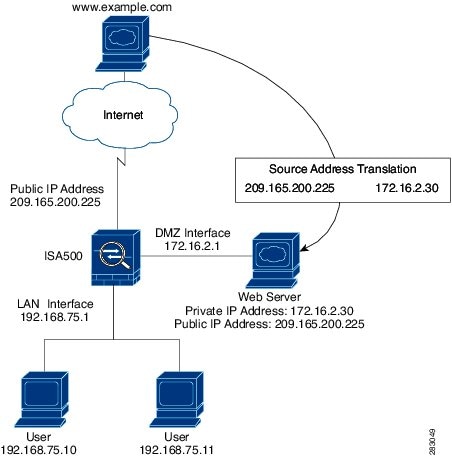
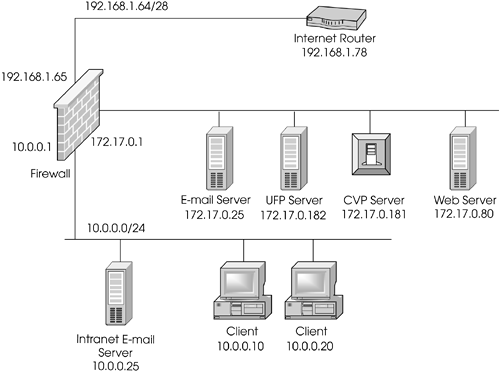
Configure Static Routing on Cisco ASA Firewall - Static ... My Network Diagram being like this I have one Adsl router it has been directly connected to ASA firewall e0 i assigned my public ip in e0 then i assigned local ip address in e1.e1 ip address is 192.168.2.1 subnet mask is 255.255.255.0 this line goes to connect to my server.my server ip address is 192.168.2.5 snm 255.255.255.0.
Network Diagrams:Zones on a diagram with Visio shape union I'll assume that you have read some of the other posts on Network Diagrams and know how to put this diagram together. Start by drawing the box that you want to represent the area: Duplicate that box (Control-D), and rotate (Control-R) and then make it a bit smaller with your mouse. Now select all the three objects, then Shape, Operations, Union.
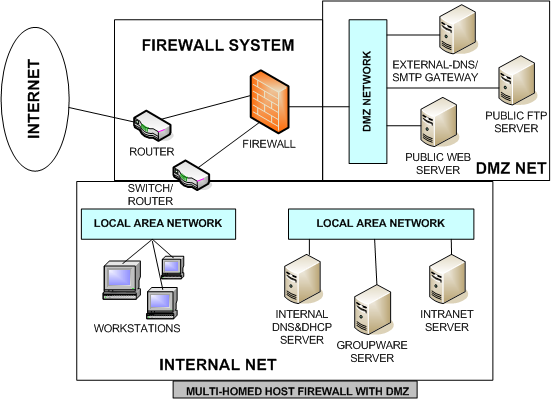
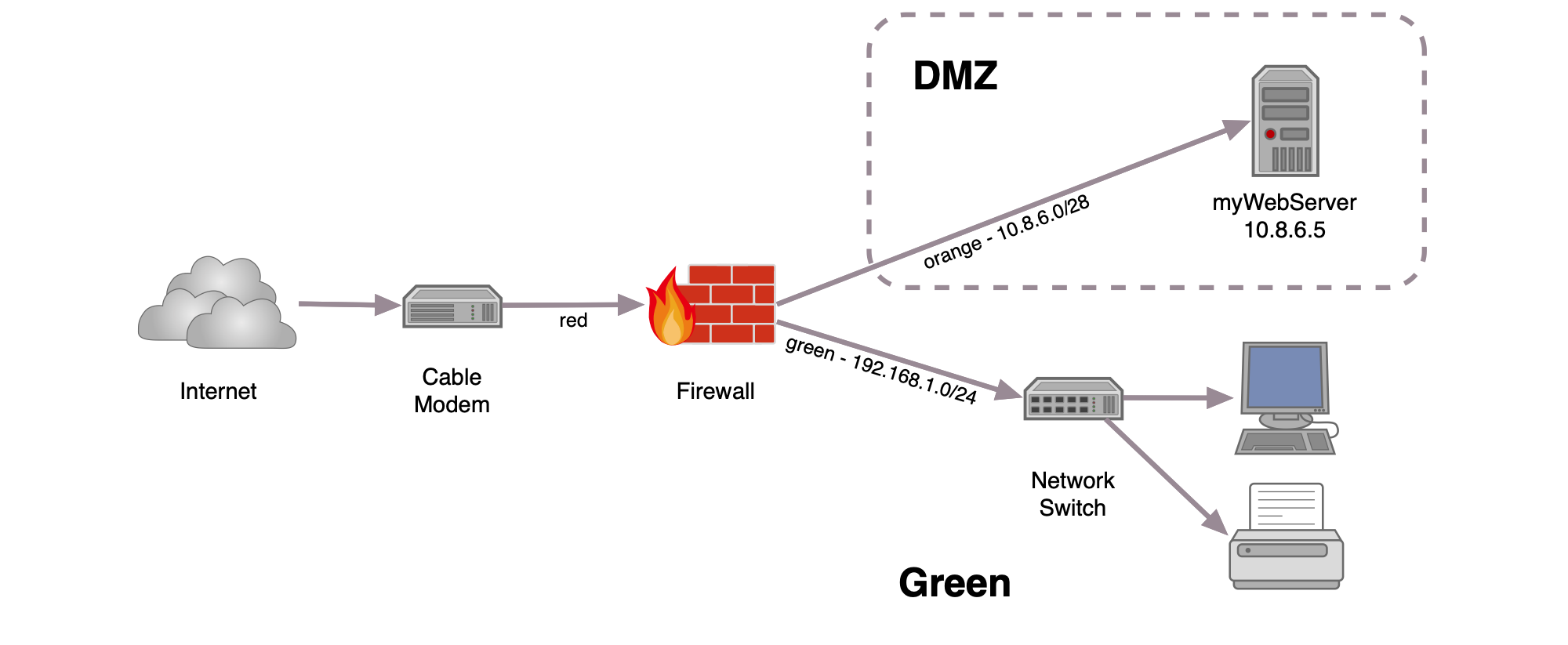
Section 2.2. Types of Firewall and DMZ Architectures ... In a DMZ (DeMilitarized Zone) network! 2.2.2 The "Three-Homed Firewall" DMZ Architecture. At its simplest, a DMZ is any network reachable by the public but isolated from one's internal network. Ideally, however, a DMZ is also protected by the firewall. Figure 2-2 shows my preferred Firewall/DMZ architecture. Figure 2-2.
support.citrix.com › article › CTX113250Required Ports for Citrix NetScaler Gateway in DMZ Setup The preceding diagram shows an example of a NetScaler Gateway configuration that involves a Single DMZ accessing Web Interface, the Secure Ticketing Authority (STA) and Presentation Server over ports 1494 and 2598 using Common Gateway Protocol (CGP).
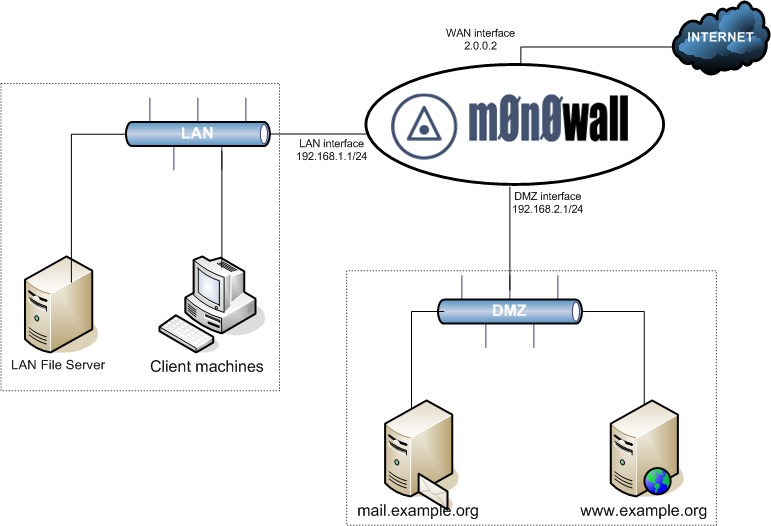
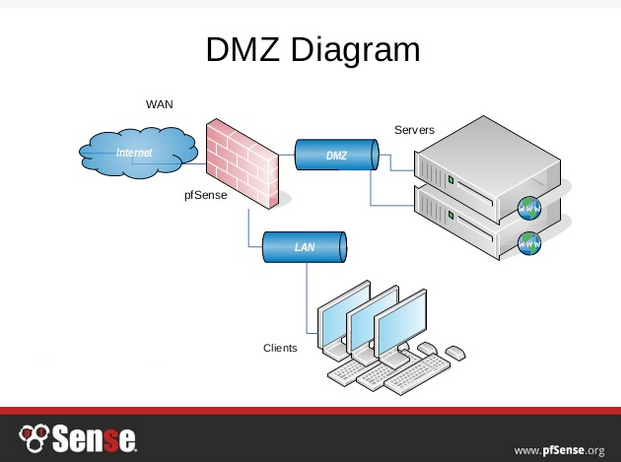
Chapter 13. Example Configurations - m0n0wall Example Network Diagram This depicts the network layout we will have after configuring our DMZ interface. 13.1.2. Adding the Optional Interface Log into your m0n0wall's webGUI, and click " (assign)" next to Interfaces. Click the on this page to add your third interface. Now restart your m0n0wall for the changes to take affect. 13.1.3.
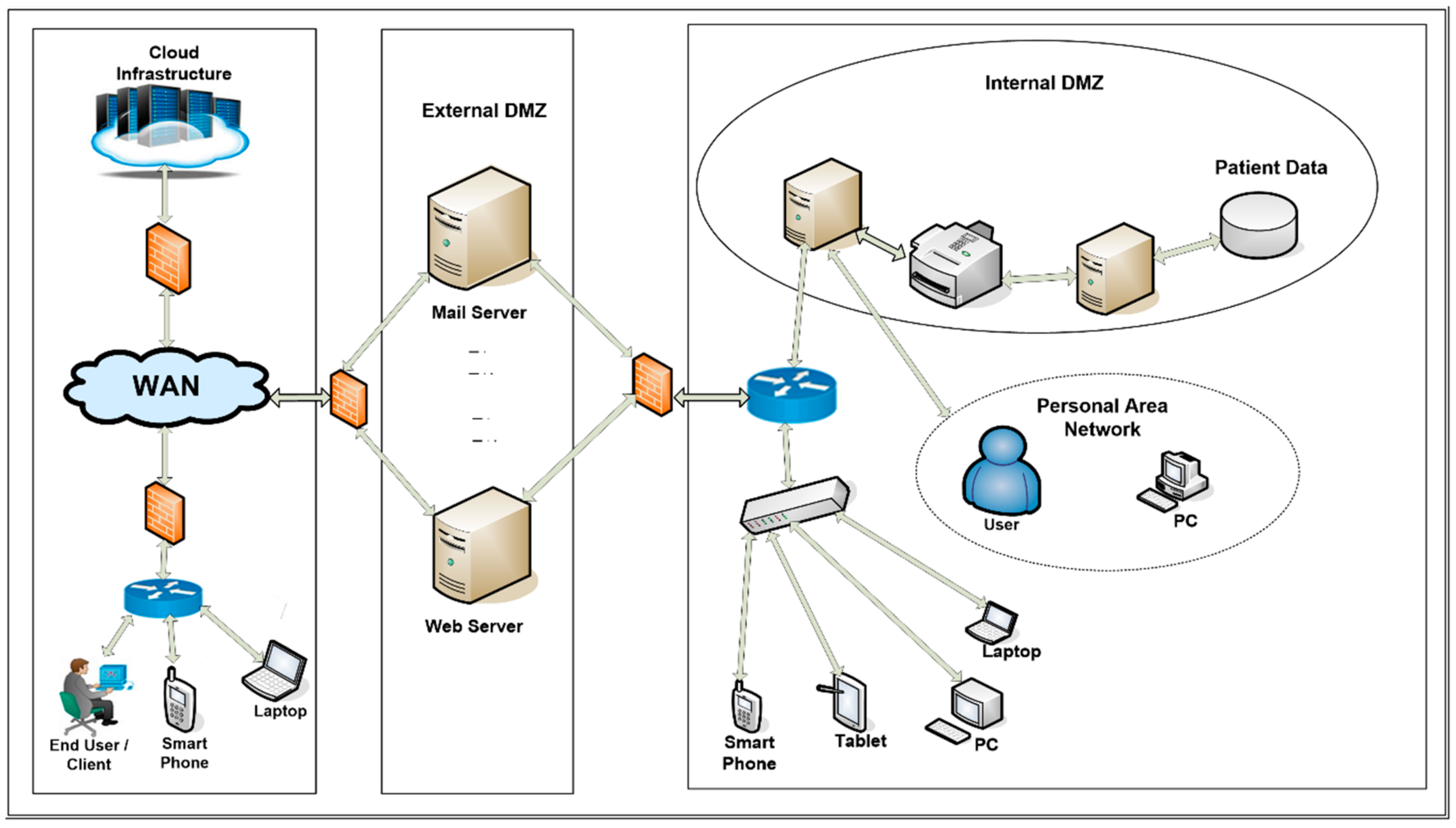
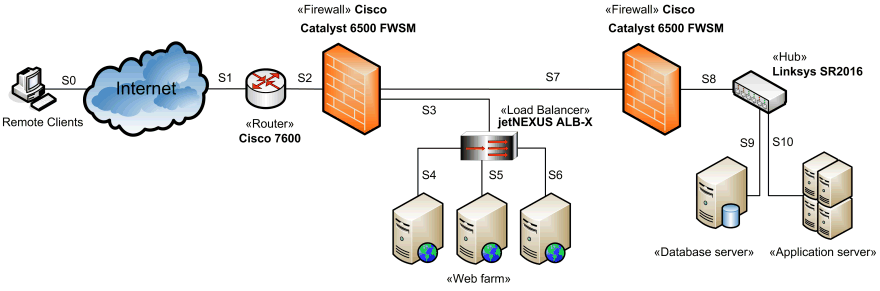
Diagram: A more complex Network Diagram (example) - A ... Figure 1 shows a more complex example of a Network Diagram. The solution constructed consists of a user interface client application run on the user's workstation, an application-server tier that consist of static HTTP content as well as services and a database tier. In addition, the solution is designed for availability, scalability and ...
Dmz Diagram Example - Diagram Sketch Dmz Diagram Example. A Medium Size Network With A Dmz Download Scientific Diagram. 1 Simple Single Firewall Dmz Download Scientific Diagram. Web Application Network Diagram Example For Online Shopping With Configuration Called Two Firewall Demilitarized Zone Dmz. Programming 3 Analyzing Delay Against The Implementation Of Dmz On Server Network ...
What Is a DMZ and Why Would You Use It? | Fortinet A DMZ Network is a perimeter network that protects and adds an extra layer of security to an organization's internal local-area network from untrusted traffic. A common DMZ is a subnetwork that sits between the public internet and private networks. The end goal of a DMZ is to allow an organization to access untrusted networks, such as the internet, while ensuring its private network or LAN ...
› How-To-Guide › Local-Area-NetworkLocal area network (LAN). Computer and Network Examples Shows the basic network components, network structure, and determines the interaction of all network devices. The diagram displays basic devices and zones: Internet, DMZ, LAN, and group. Clarifies what network equipment is connected, describes the major nodes in the network, gives an understanding of the logical structure of the network as well ...
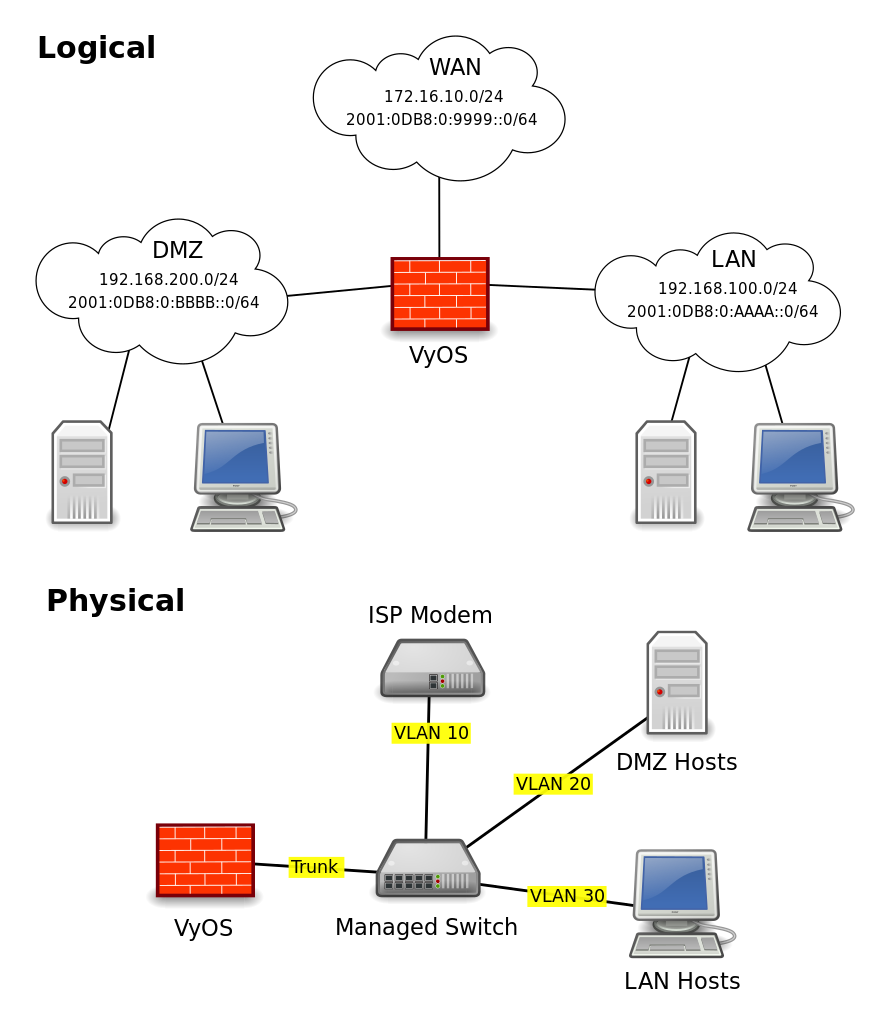
› articles › how-to-install-aHow to Configure a Demilitarized Zone Network - DMZ Server ... Jun 26, 2020 · Here’s a diagram of the final DMZ network setup: This configuration is also known as the three-legged model. To take security up a notch, you can also use two firewalls (the back-to-back model). In this setup, one of the firewalls will allow traffic destined to the DMZ only, while the other only allows traffic to the DMZ from the internal ...
docs.microsoft.com › en-us › azureImplement a secure hybrid network - Azure Architecture Center ... Network security groups.Use security groups to restrict network traffic within the virtual network. For example, in the deployment provided with this reference architecture, the web tier subnet allows TCP traffic from the on-premises network and from within the virtual network; the business tier allows traffic from the web tier, and the data tier allows traffic from the business tier.
Web application network diagram example for online ... The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network).
Firewall DMZ Configuration | EdrawMax Editable Templates The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network). It prevents outside users from gaining direct access to an organization's internal network while not ...










![Determining our deployment scenario - pfSense 2.x Cookbook [Book]](https://www.oreilly.com/library/view/pfsense-2x-cookbook/9781789806427/assets/0287d11c-c368-4aa0-99f3-6b030dfc1720.png)









0 Response to "39 dmz network diagram example"
Post a Comment